TL;DR
This writeup covers the Preignition machine, a beginner-friendly Linux box on Hack The Box. The initial Nmap scan revealed an open HTTP port (80) running Nginx. Directory fuzzing with dirb uncovered an admin.php page, leading to a login panel. I attempted common default credentials, and the combination admin:admin successfully granted access to the admin console. From here, further exploitation was possible to gain system access.
Scanning Network
I began by performing an Nmap scan, which revealed an open port, 80, corresponding to http. Here are the results from the Nmap scan:
1
2
3
4
5
6
7
8
9
10
11
12
| nmap -sC -sV -A -T4 -Pn 10.129.12.119 -oN scan/normal.scan
Starting Nmap 7.94 ( https://nmap.org ) at 2025-02-15 22:08 IST
Nmap scan report for 10.129.12.119
Host is up (0.22s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.14.2
5633/tcp filtered beorl
9594/tcp filtered msgsys
32772/tcp filtered sometimes-rpc7
|
Enumeration
While analyzing the Nmap output, I found that port 80 was open. Since this is the only open port, I decided to perform directory fuzzing to discover interesting directories, files, or endpoints.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| dirb http://10.129.12.119/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Feb 15 22:14:26 2025
URL_BASE: http://10.129.12.119/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.129.12.119/ ----
+ http://10.129.12.119/admin.php (CODE:200|SIZE:999)
|
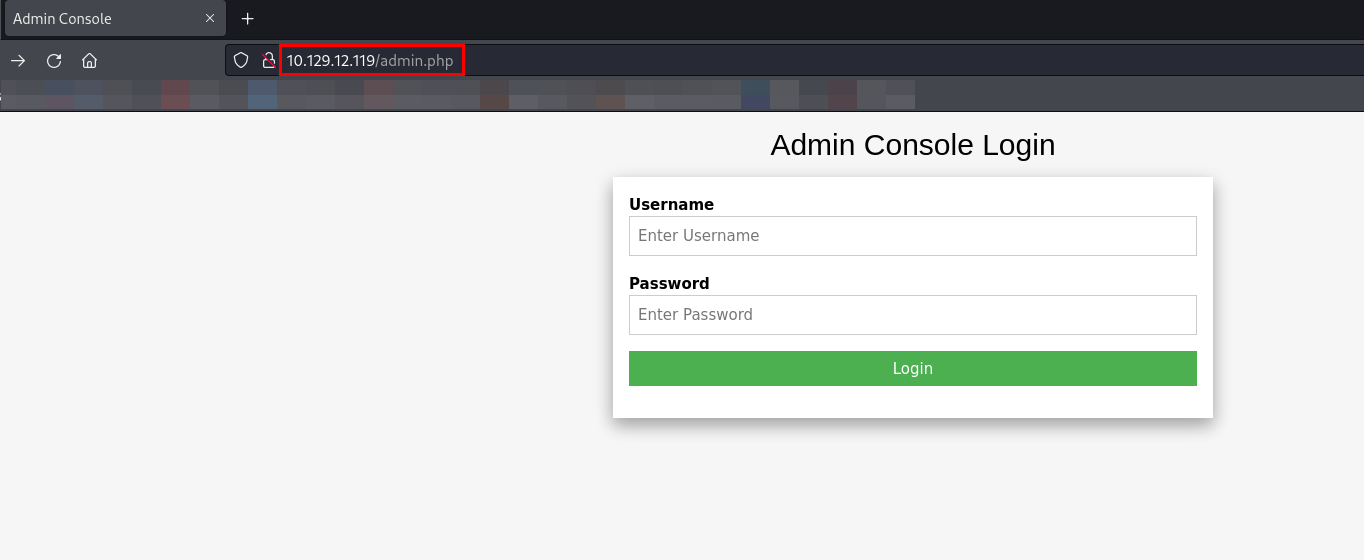
Let’s visit http://10.129.12.119/admin.php.
I discovered a login page for an admin console. Typically, admin consoles use default usernames such as admin, administrator, or root, with common passwords like adminor password.
I attempted various username/password combinations to log in to the admin console.
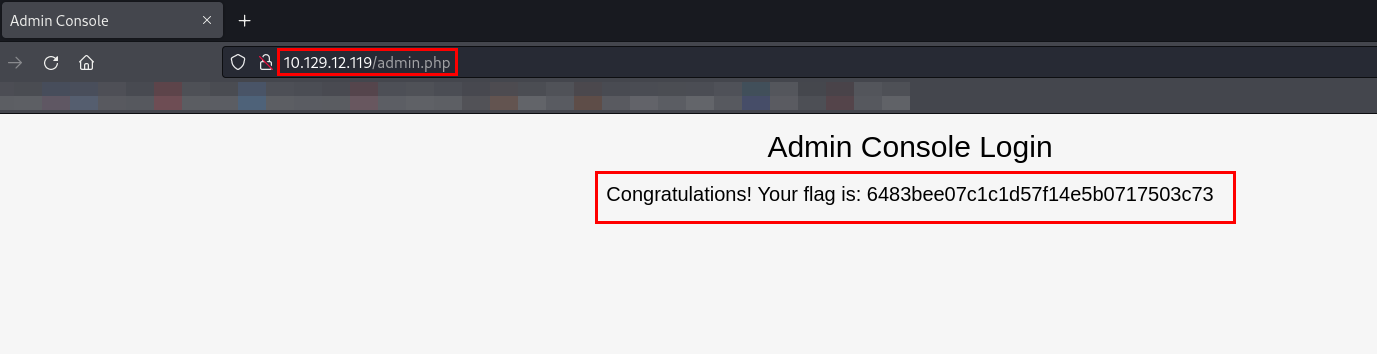
After testing multiple possibilities, the combination admin:admin was successful, granting me access to the admin console.
Tasks
Directory Brute-forcing is a technique used to check a lot of paths on a web server to find hidden pages. Which is another name for this? (i) Local File Inclusion, (ii) dir busting, (iii) hash cracking.
What does Nmap report is the service identified as running on port 80/tcp?
What server name and version of service is running on port 80/tcp?
When using gobuster to dir bust, what switch do we add to make sure it finds PHP pages?
What page is found during our dir busting activities?
What is the HTTP status code reported by Gobuster for the discovered page?
Submit root flag
1
| 6483bee07c1c1d57f14e5b0717503c73
|
Thanks for reading this far. If you enjoyed the writeup, do support me here.